This guide shows how to SSH into Linux safely and confidently. It covers what SSH is, how to prepare the remote Linux server, how to connect from Windows, macOS, and Linux, how to use both passwords and SSH keys, and how to fix common problems. The tone is practical and focused on real steps that work.
SSH in simple terms
SSH means Secure Shell. It creates an encrypted connection between your computer and a remote Linux machine. With SSH you can:
- Run commands on a remote server
- Transfer files securely with SCP or SFTP
- Forward network ports through an encrypted tunnel
Three parts matter:
- SSH client on your computer
- SSH server on the Linux machine
- Encryption that protects everything sent over the network
Prerequisites checklist
Remote Linux server
- OpenSSH server installed
- SSH service running
- Firewall or cloud security group allows TCP port 22 or another chosen port
- IP address or DNS hostname available
- A user account on the server
Your computer
- SSH client installed
- Windows 10 or 11 OpenSSH client or PuTTY
- macOS Terminal with OpenSSH
- Linux OpenSSH client
- Network access to the server
- Username and either a password or an SSH key pair
New to Linux distributions
Understand how distributions differ and choose the right one for your server setup. Clear comparisons, use cases, and guidance.
Prepare the remote Linux server
Run these on the server.
OpenSSH is the standard SSH implementation: OpenSSH project.
# Install OpenSSH server
# Debian or Ubuntu
sudo apt update
sudo apt install -y openssh-server
# RHEL, Rocky, AlmaLinux
sudo dnf install -y openssh-server
# (Older RHEL or CentOS may use: sudo yum install -y openssh-server)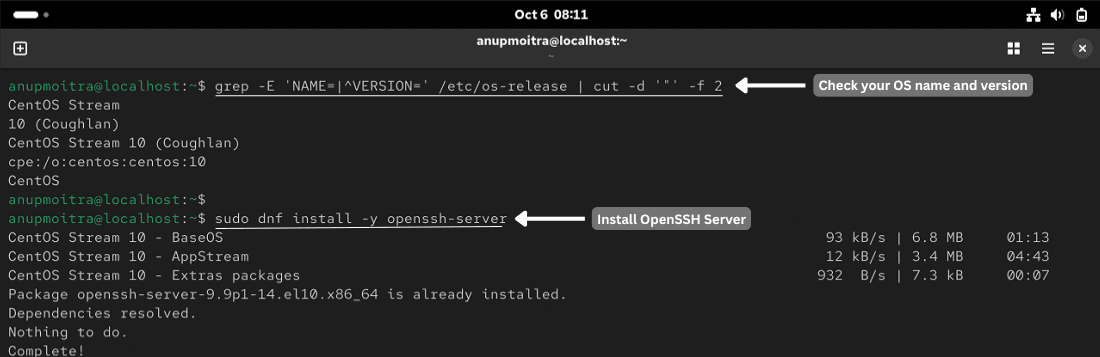
# Start and enable the service
# Debian or Ubuntu
sudo systemctl enable --now ssh
# RHEL family
sudo systemctl enable --now sshd
# Verify status
sudo systemctl status ssh # Debian or Ubuntu
sudo systemctl status sshd # RHEL family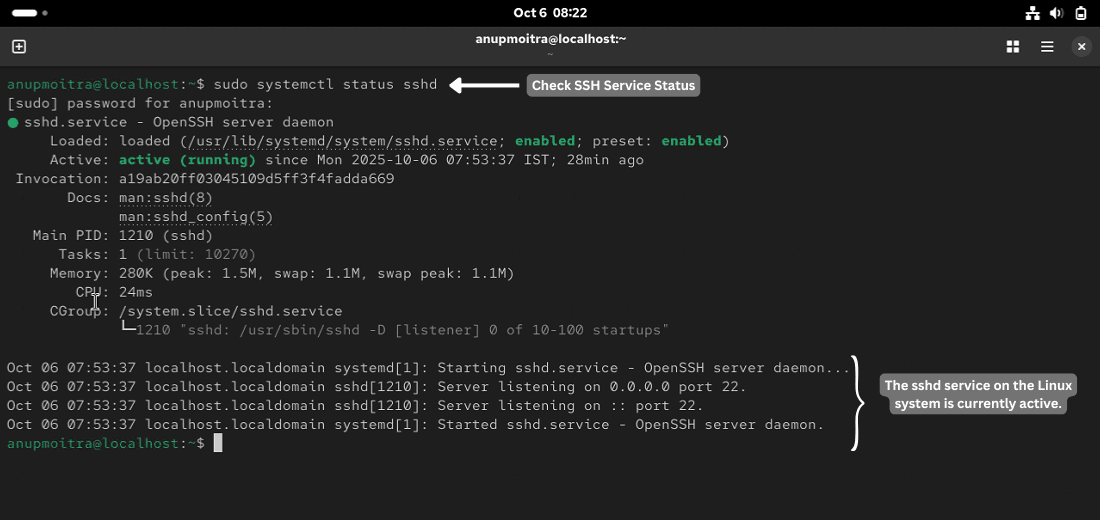
# Open the firewall
# UFW on Ubuntu
sudo ufw allow OpenSSH
sudo ufw enable # if UFW is not already enabled
sudo ufw status
# firewalld on RHEL family
sudo firewall-cmd --permanent --add-service=ssh
sudo firewall-cmd --reload
# Cloud servers: allow the SSH port in the instance security groupFirewall reference: UFW on Ubuntu Server.
# Find the server address
ip a
# or
hostname -I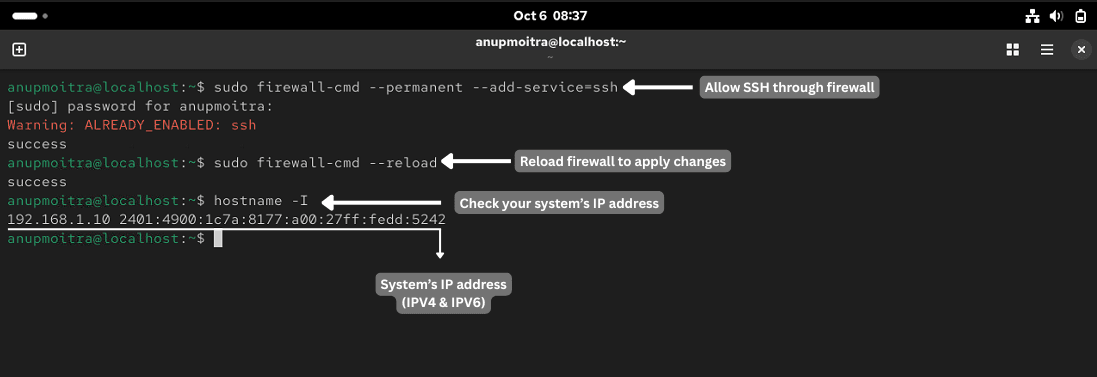
How to SSH into Linux from your computer
Quick reference table
| Step | Windows OpenSSH | Windows PuTTY | macOS | Linux |
|---|---|---|---|---|
| Launch client | PowerShell or Command Prompt | PuTTY | Terminal | Terminal |
| Connect | ssh user@host | Enter host and Open | ssh user@host | ssh user@host |
| First time | Type yes to trust host key | Accept host key prompt | Type yes | Type yes |
| Authenticate | Password or key | Password or key | Password or key | Password or key |
| Disconnect | exit | Close or exit | exit | exit |
Note: In examples we use 203.0.113.10 (a documentation-only IP). Replace it with your server IP or hostname — for example 192.168.1.10 or myserver.example.com.
Windows 10 and 11 with the built-in OpenSSH client
- Check the client: Settings → Apps → Optional Features → OpenSSH Client. If missing, add it.
- Open PowerShell or Command Prompt.
- Connect
# Replace 203.0.113.10 with your server IP/hostname (e.g., 192.168.1.10)
ssh user@203.0.113.10
# On first connect, type yes to trust the host key.
# Enter the account password when prompted. No characters appear while typing.# Useful options
# (use -p if your SSH server listens on a non-default port)
ssh -p 2222 user@203.0.113.10 # custom port
ssh -v user@203.0.113.10 # verbose output for troubleshooting
# Exit
exit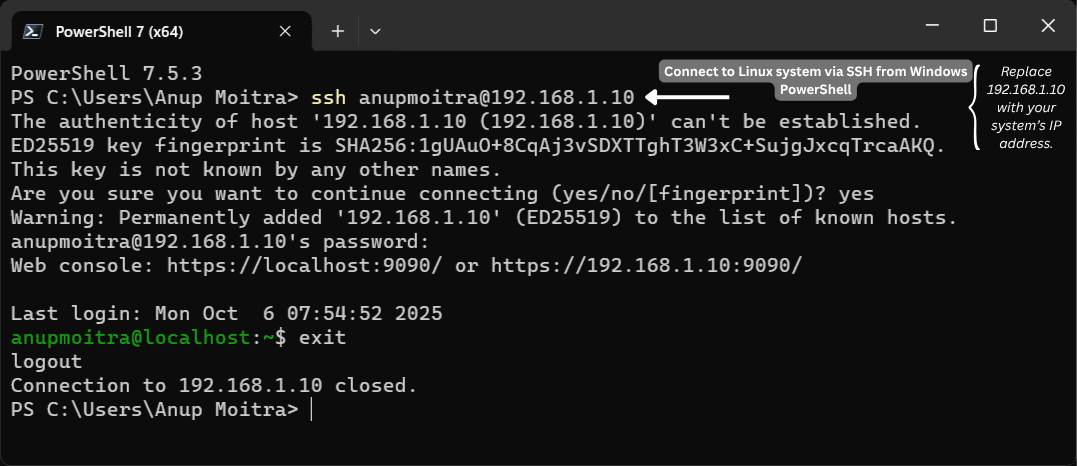
Microsoft reference: Windows OpenSSH docs.
Windows with PuTTY
- Download and install from the official site.
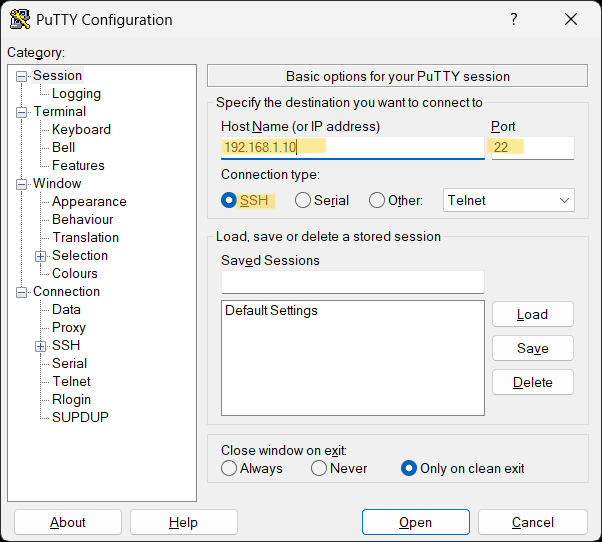
- Open PuTTY → Session and set:
- Host Name:
192.168.1.10(replace with your server IP or hostname) - Port:
22 - Connection type: SSH
- Host Name:
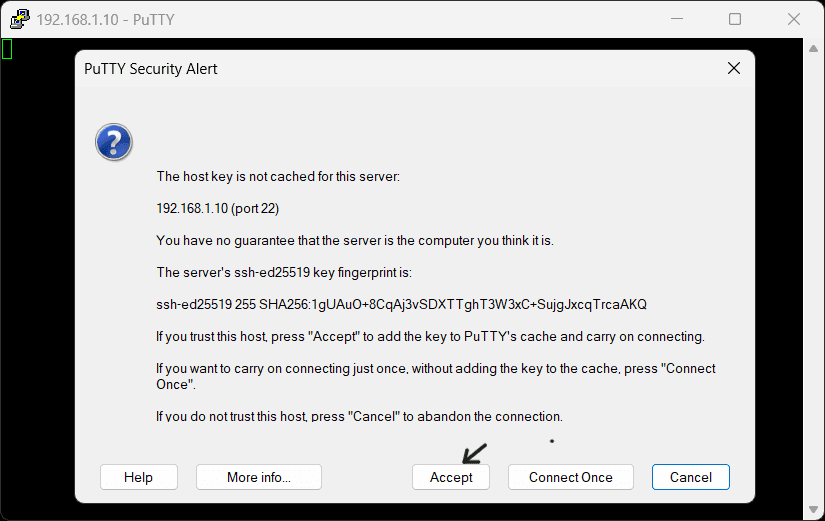
- Click Open, then accept the first-time security alert.
- Enter your username, then your password.
- Type
exitto close.
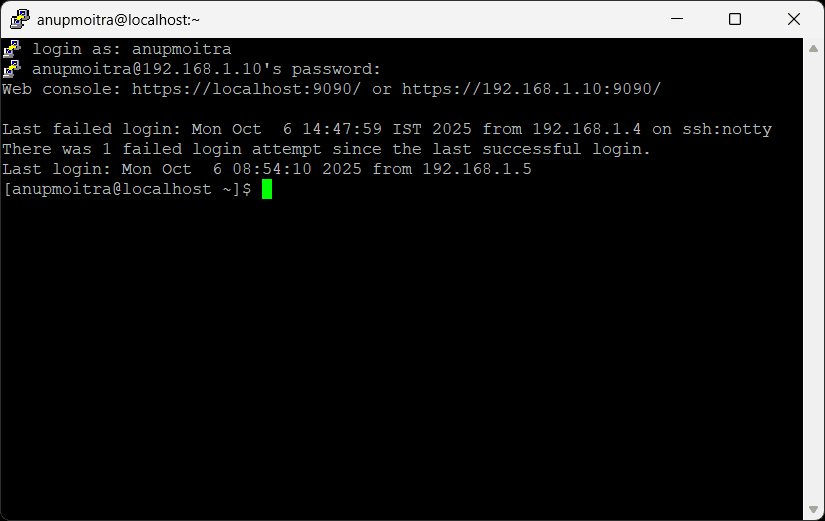
macOS
# Replace 203.0.113.10 with your server IP/hostname (e.g., 192.168.1.10)
ssh user@203.0.113.10
# First time, type yes to trust the host key, then enter the password.
# Exit with:
exit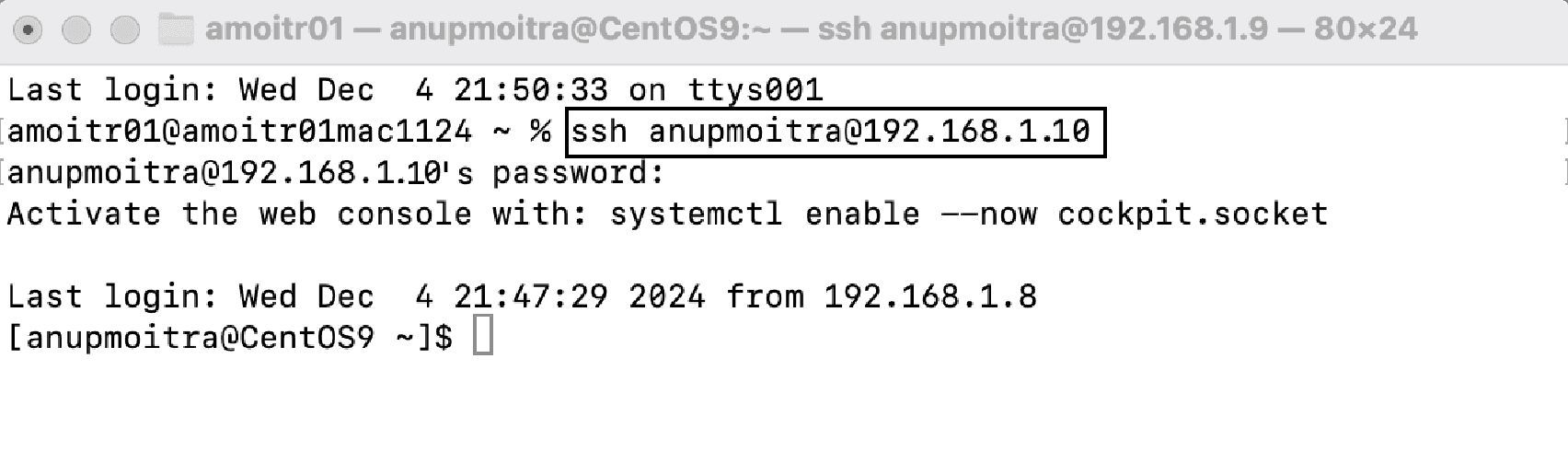
Linux
# Replace 203.0.113.10 with your server IP/hostname (e.g., 192.168.1.10)
ssh user@203.0.113.10
# Accept the host key and enter the password.
# Exit with:
exit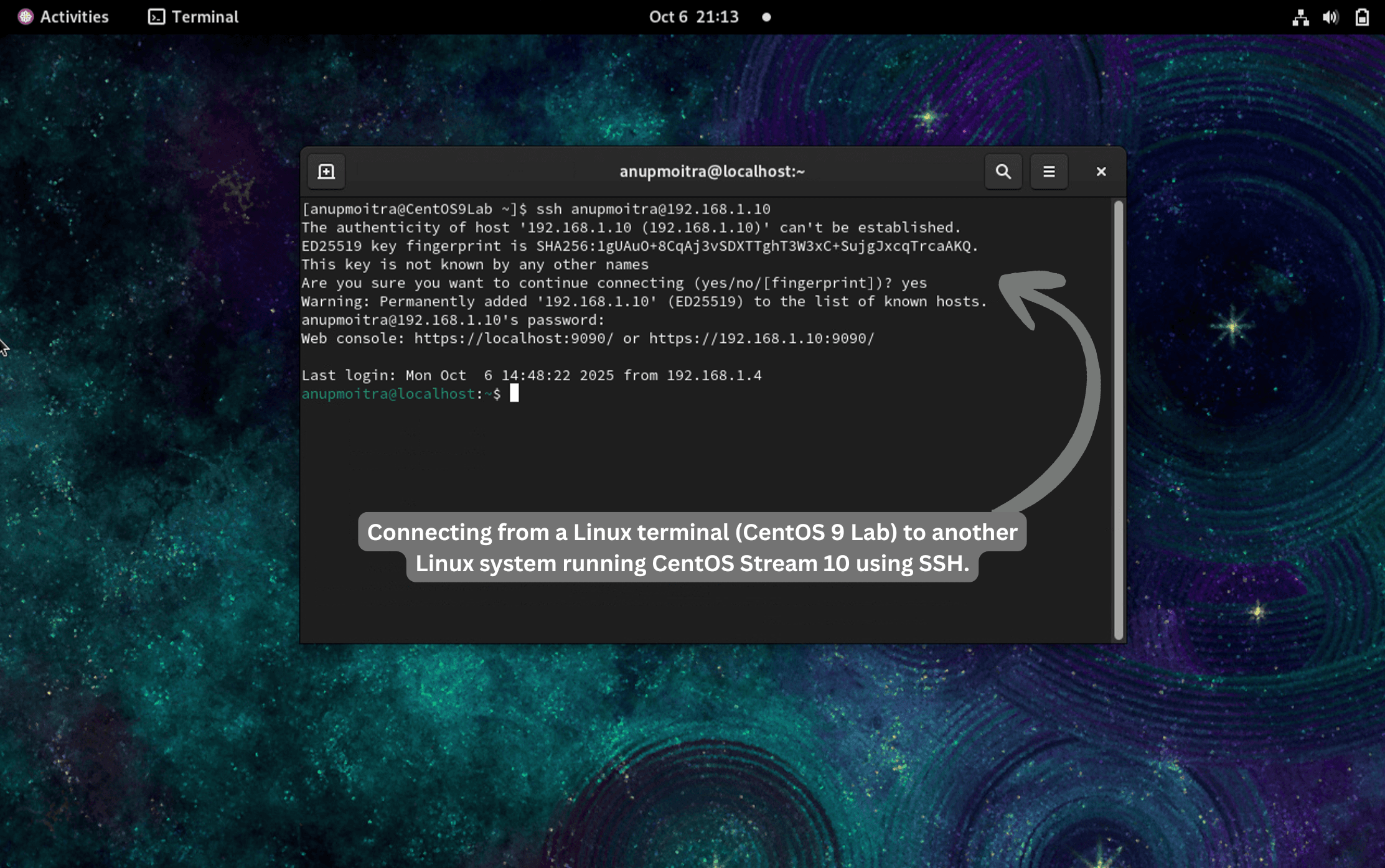
Password login and SSH keys
Password login is simple for first use. SSH keys improve security and convenience.
Generate a key pair on your computer
# Recommended modern key
ssh-keygen -t ed25519 -C "your_label"
# Traditional RSA option
ssh-keygen -t rsa -b 4096 -C "your_label"
# Press Enter to accept the default path ~/.ssh/id_ed25519 or ~/.ssh/id_rsa
# Choose a passphrase for the private key for better securityPuTTY users on Windows: open PuTTYgen, choose Ed25519 or RSA 4096, click Generate, save the private key .ppk, and copy the public key text.
Install your public key on the server
# Automatic method
# Replace 203.0.113.10 with your server IP/hostname (e.g., 192.168.1.10)
ssh-copy-id user@203.0.113.10
# Enter the server password one time. The tool appends your public key to ~/.ssh/authorized_keys# Manual method
# On your computer
cat ~/.ssh/id_ed25519.pub
# Copy the single line
# On the server
mkdir -p ~/.ssh
chmod 700 ~/.ssh
echo "ssh-ed25519 AAAA... your_label" >> ~/.ssh/authorized_keys
chmod 600 ~/.ssh/authorized_keysLog in with your key
# Replace 203.0.113.10 with your server IP/hostname (e.g., 192.168.1.10)
ssh user@203.0.113.10
# If your key has a passphrase, the client will ask to unlock it.Use an SSH agent
# macOS and Linux
eval "$(ssh-agent -s)"
ssh-add ~/.ssh/id_ed25519# Windows OpenSSH (PowerShell)
Get-Service ssh-agent
Start-Service ssh-agent
Set-Service -Name ssh-agent -StartupType Automatic
ssh-add $env:USERPROFILE\.ssh\id_ed25519PuTTY with keys
In PuTTY, go to Connection → SSH → Auth, pick your .ppk private key, return to Session, and connect.
Optional hardening after keys work
# Edit /etc/ssh/sshd_config on the server
PermitRootLogin no
PasswordAuthentication no
ChallengeResponseAuthentication no
# Reload
sudo systemctl reload ssh # Debian or Ubuntu
sudo systemctl reload sshd # RHEL family
# SELinux note for non-standard port
sudo semanage port -a -t ssh_port_t -p tcp 2222
sudo systemctl reload sshd
# Install policycoreutils-python-utils if semanage is missingEveryday usage
Shortcuts with ~/.ssh/config on your computer
# Replace HostName with your server IP/hostname (e.g., 192.168.1.10)
Host myserver
HostName 203.0.113.10
User user
Port 22
IdentityFile ~/.ssh/id_ed25519
# Connect with:
# ssh myserverCopy files
# SCP upload
scp file.txt user@203.0.113.10:/home/user/
# SCP download
scp user@203.0.113.10:/etc/hosts .
# SFTP interactive session
sftp user@203.0.113.10
# then: put, get, ls, cd, lcd, pwd, exitPort forwarding
# Local forward example
ssh -L 8080:localhost:80 user@203.0.113.10
# Open http://localhost:8080 on your computerX11 forwarding for graphical apps
# Client side
ssh -X user@203.0.113.10
# Server and client must both support X11Troubleshooting how to SSH into Linux
Cannot reach the server
Connection refused: The service is not listening or the port is wrong.
sudo systemctl status ssh # Debian or Ubuntu
sudo systemctl status sshd # RHEL family
# Check the port and use -p if it is not 22Connection timed out: A firewall or network path is blocking traffic.
# Replace 203.0.113.10 with your server IP/hostname
ping 203.0.113.10
nc -vz 203.0.113.10 22 # or: telnet 203.0.113.10 22
# Open the port in host and cloud firewallsAuthentication problems
Permission denied (password): Wrong username or password, or password login disabled. Confirm the account and settings in /etc/ssh/sshd_config.
Permission denied (publickey): The server cannot use your key. Fix permissions and ensure the correct key.
chmod 700 ~/.ssh
chmod 600 ~/.ssh/authorized_keys
# Replace with your key path and server IP/hostname
ssh -i ~/.ssh/id_ed25519 user@203.0.113.10Host key warnings
Host key verification failed or remote host identification has changed. Verify that the server really changed. Then clear the cached key and reconnect.
# Replace 203.0.113.10 with your server IP/hostname
ssh-keygen -R 203.0.113.10
# or edit ~/.ssh/known_hostsVerbose client output
ssh -vvv user@203.0.113.10Server logs
# Debian or Ubuntu
sudo tail -f /var/log/auth.log
# RHEL family
sudo tail -f /var/log/secureClient not found
# Debian or Ubuntu
sudo apt install -y openssh-client
# RHEL family
sudo dnf install -y openssh-clients
# Windows: install the OpenSSH Client optional feature or use PuTTYSecurity best practices
- Prefer key-based authentication
- Disable root SSH login
- Keep packages updated
- Use fail2ban or similar to block repeated failures
- Protect private keys with a passphrase and use an agent
- Remove unused keys from
authorized_keysregularly
One-minute quick start
# On the server (Debian or Ubuntu)
sudo apt install -y openssh-server
sudo systemctl enable --now ssh
sudo ufw allow OpenSSH
# On the server (RHEL family)
sudo dnf install -y openssh-server
sudo systemctl enable --now sshd
sudo firewall-cmd --permanent --add-service=ssh
sudo firewall-cmd --reload
# On your computer
ssh-keygen -t ed25519
# Replace 203.0.113.10 with your server IP/hostname (e.g., 192.168.1.10)
ssh-copy-id user@203.0.113.10
ssh user@203.0.113.10Frequently asked questions
Is SSH safe over the internet
What if the server uses a different port
-p PORT to the SSH command or set Port in ~/.ssh/config.Can I run graphical apps through SSH
How do I share files easily
Conclusion
You now know how to SSH into Linux from Windows, macOS, and Linux. You can prepare the server, connect with either a password or keys, transfer files, forward ports, and troubleshoot issues with confidence.